- Articles
- A Guide to Azure Identity Protection Licenses
Table of Contents
Many are hiring entire IT teams, buying antivirus software, and setting up firewalls.
But here's a threat many are missing - their own employees.
While companies are shoring up their external defenses, an employee with a weak password can put their entire organization in danger.After all, an estimated 81% of data breaches are due to poor password security, and 1 in 8 employees are likely to share information requested in a phishing email.
If an attacker gains access to an employee's credentials, all the antivirus programs in the world won't stop them from wreaking havoc on your network and systems.
Companies need a tool like Azure Identity Protection to fix that weak spot. Azure Identity Protection can identify suspicious user behavior, flag potential threats, and offer companies the chance to respond to attacks effectively.
Interested in learning more?
Excellent; here's what we'll cover in this blog post:
- What is Azure AD Identity Protection?
- The 4 types of Azure Identity Protection
- The 4 benefits of Azure Identity Protection
- How to get started with an Azure Identity Protection license
- Azure Identity Protection FAQs
Let's dive in.
What Is Azure AD Identity Protection?

Azure AD Identity Protection is a security tool that detects identity-based risks, like compromised identities and security credentials. This software solution mitigates security threats and provides information on security events that help organizations with their investigations. Essentially, Azure Identity Protection safeguards individuals and organizations from identity-based threats and helps with remediation efforts if an attack occurs.
Azure identity protection offers three identity protection policies:
1. Multi-factor authentication registration policy
Multi-factor authentication (MFA) requires more than one piece of evidence to confirm a user's identity before allowing access to an account, system, network, or website.
Organizations can choose Azure multi-factor authentication for every one of their members.
If organizations allow users access to their networks and systems based only on one-factor authentication, like a single password, they leave themselves open to an attack. But if they implement Multi-factor authentication, then, according to Microsoft, they will block 99.9% of compromise attacks.
MFA essentially demands a second confirmation of identity. This can be a fingerprint, a face scan, or another trusted device or application like a mobile phone or email.
It's hard for attackers to access these secondary applications and devices. That's why multi-factor authentication drastically decreases the risk of successful identity theft.
2. Sign-in risk policy
This Azure Identity Protection policy calculates the probability that a sign-in has been compromised.
Organizations can create a customer policy where they select the user's location, device, and other factors as pre-set conditions.
That doesn't mean that users can't access a system unless they're using their phone and standing in a specific location in their office - it just means that, based on these conditions, the program calculates a risk score.
The risk score determines the likelihood of an identity-based attack depending on any deviation from normal user behavior.
If an employee usually accesses the company system in their office from their laptop, and then one day, someone tries to access it from their phone while at the top of the Eiffel tower, the system will flag the attempt.
Based on that score, the administrator can decide whether they will allow the user access to the system.
They can:
- Block access
- Allow access
- Require multi-factor authentication
Sometimes, the system will flag the attempt to sign in, but the administrator will have direct access to the user and can confirm their identity immediately.
But with the rise of remote and hybrid work, that is often not the case anymore. The administrator might demand multi-factor authentication to protect the organization's network or system.
3. User risk policy
This Azure Identity Protection feature calculates the probability that attackers have compromised the system using a current user's identity.
Azure Identity Protection considers normal user behavior and uses that calculation to determine the risk of user impersonation.
Based on that calculation, Azure Active Directory Identity Protection sends a signal to the administrators, who can decide if they will block access or allow it.
If the risk is detected, the users can remediate the problem by resetting the password and ensuring the administrator doesn't receive too many signals.
The 4 Types of Azure Identity Protection

1. User
Employees and guests who use Azure Identity Protection fall under the category of user identities. Based on these identities, administrators grant access authorizations to individual employees based on the requirements of their jobs.
However, if several users have the same authorization levels, such as employees with similar tasks, then the administrator can create a group. Instead of assigning access individually, the administrator can simplify the process by managing the entire group.
2. Service principal
A service principal is a secure identity that gives services or apps the authorization to access Azure resources.
In layperson's terms, it's an application's version of user identity. They're necessary in case employees need to access Azure resources through an application. The service principal ensures that this process doesn't present a security risk to the organization.
A service principal is created in each tenant where the application is used. The service principal defines who uses the app and what resources the app can access.
3. Managed identity
A managed identity is an identity controlled by the Azure Active Directory. Organizations typically use them to control the credentials of cloud applications with an Azure service.
There are two types of managed identities:
- System-assigned: This type is enabled directly on an Azure resource instance. When you create a system-assigned managed identity, you also create an identity in Azure AD, which is then tied to the life cycle of that service instance. When you delete the resource, Azure automatically deletes the resource for the user.
- User-assigned: This type allows users to create a managed identity as a standalone Azure resource. For user-assigned managed identities, the identity is managed separately from the resources that use it.
4. Device
Companies can set up device identities for any of their hardware, whether mobile phones, printers, laptops, etc. Companies can set up these identities based on different determining properties, like who owns the device. The device's authorizations are then assigned based on that information.
The 4 Benefits of Azure Identity Protection
1. Risk identification
Risk identification in Azure Identity Protection means finding any suspicious activities related to a specific user account. Through the user risk policy and sign-in risk policy, Azure Identity Protection creates an overall risk score that the administrators can view in the Risky Users report. The report defines three risk levels: low, medium, and high.
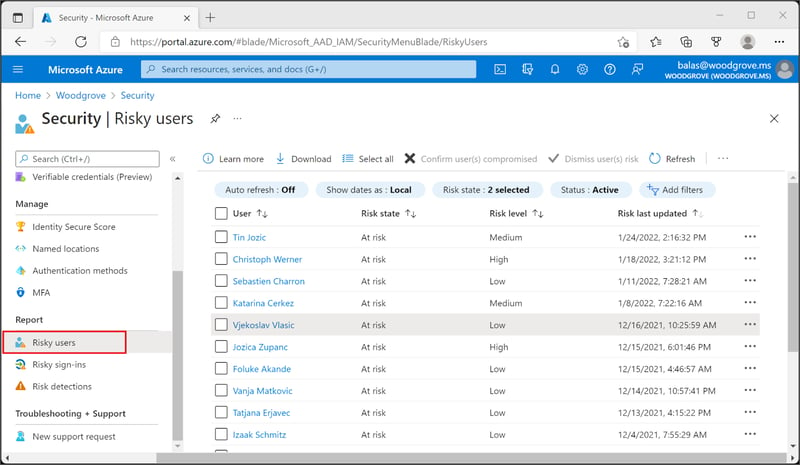
Azure Identity Protection offers organizations the chance to quickly identify risks and respond to them through these tools.
2. Remediation triggers
After Azure Identity Protection has flagged risky users and sign-ins, the tool allows administrators to begin with remediation immediately.
Remediation in cyber security is the process of containing and eliminating threats to an organization's system or network.
With Azure Identity Protection, organizations benefit from a tool that allows them to trigger specific actions and respond to threats efficiently.
The options to remediate threats available to administrators are:
- Self-remediation with risk policy
- Manual password reset
- Dismissing user risk
Self-remediation with risk policy means that users can unblock their profiles on their own with multi-factor authentication (MFA) and self-service password reset (SSPR). But users must have previously registered for Azure AD MFA and SSPR.
Manual password resets allow administrators to close the risk detection by generating a temporary password. The user is contacted with the new password, but they choose a new one the next time they sign in.
Dismissing user risk is an option for administrators who determine the user identity isn't threatened - they can dismiss the risk detection without requiring any action from the user.
3. Better intelligence
Azure Identity Protection uses machine learning to create a baseline of user behavior.
This feature provides the company with better intelligence as Azure Identity Protection discovers suspicious activity far quicker than it otherwise could, allowing the company to respond to potential threats before they can cause serious harm to the company.
With Azure Identity Protection, organizations get their hands on a tool that drastically reduces their attack surface, minimizing the risk of a potential cyber attack without requiring great investments from organizations.
4. Safer remote working
With the rise of remote working, many employees work from unsecured devices and open home WiFi networks that are far more vulnerable to potential attacks.
It's no wonder that 80% of security and business leaders said their organizations are more exposed to risk due to remote work.
The increased risks also show themselves in the costs of data breaches - remote work has caused the average cost of a data breach to go up by $137,000.
That's why adopting Azure Identity Protection is an excellent idea for any company relying heavily on remote work.
Authenticating user identities ensures no outside threat gains access to the company networks. And by monitoring user behavior, Azure Identity Protection quickly flags users whose identities have been compromised, whether through phishing emails or other methods.
Azure Identity Protection Licenses: Azure PD Premium P1 vs P2

Azure AD Premium P1
Azure AD Premium P1 is an enterprise-level edition of Azure's Active Directory.
Among the features it offers its users is identity management for on-premise users, remote users, and those who straddle the fence between the two.
Among the features offered by Azure AD Premium P1 are:
- Unlimited Directory objects
- Unlimited single sign-on apps
- Password protection
- Group access management
- Advanced security analysis reports
- And many others
Azure AD Premium P1 costs companies $6/user per month.
Azure AD Premium P2
Azure AD Premium P2 offers all the features offered by Azure AD Premium P1.
But there are additional features available with this license. For one, Azure Identity Protection is only available with Azure AD Premium P2.
Additionally, the license also offers:
- Identity governance
- Event logging and reporting
- Privileged identity management
Azure Premium P2 costs companies $9/user per month.
Azure AD Premium P1 vs Azure AD Premium P2 comparison table
|
Features |
Azure AD Premium P1 |
Azure AD Premium P2 |
|
Authentication, Single Sign-On, MFA |
✔ | ✔ |
|
Application access |
✔ | ✔ |
|
Authorization and conditional access |
✔ | |
|
Administration and hybrid identity |
✔ | ✔ |
|
End-user self service |
✔ | |
|
Identity governance |
✔ | |
|
Event logging and reporting |
✔ | |
|
Frontline workers |
✔ | ✔ |
|
Cost |
$6/user per month |
$9/user per month |
How To Get Started With an Azure Identity Protection License
Like with any other software solution, companies can adopt Azure Identity Protection on their own and implement it into their business processes to the best of their ability.
Unfortunately, this also comes with a number of problems. For one, companies have to decide which license they want to buy in the first place, and then they have to ensure that they take full advantage of every feature they purchase.
That's where Amaxra has helped so many companies. Through their Microsoft Licensing Optimization, they offer four main benefits:
- Saving costs: Amaxra helps ensure that its customers only pay for the licenses and features their business needs.
- Easier license management: Companies have a clear overview of the services they pay for, ensuring they don't underutilize their software tools.
- Better security: Good oversight leads to better security as companies know exactly how each potential weak point is protected and by whom. Amaxra's services also ensure all software solutions are up to date.
- Future-proofing: Optimized software makes it easier for companies to make any necessary changes. They can remove software and users at will instead of attempting to untangle complex webs of obsolete software tools.
With these benefits, companies simplify the process of acquiring security software, which can be incredibly complex and confusing. Companies save money by choosing licensing optimization and gain peace of mind knowing they've implemented the optimum solution for their business.


Need Help with Microsoft Licensing?
Leave your Microsoft licensing, security, and software solutions to us so you can concentrate on moving your business forward.Drop Us a Line
Azure Identity Protection FAQs

"What is risk detection in Azure AD Identity Protection?"
Risk detections are any suspicious actions related to user accounts in the Active Directory. Based on these risk detections, Azure Identity Protection creates a Risk Score that administrators can find in the Risky User report.
Azure Identity Protection detects risk at the user or the sign-in level. At the sign-in level, it gauges the possibility that the employee's identity may have been compromised. At the user level, it examines if the user is an intruder, one the administrator hasn't approved.
There are also two types of risk detection or calculation: real-time and offline. Real-time detection shows up in reports within the first 10 minutes. Offline detections often don't show up for the first 48 hours.
It's necessary to point out that some risks are only available to Premium users, which means they won't show up to Azure AD Premium P1 users or the Free users.
"How does Microsoft identify risky users?"
Risks are established by the system administrator when they first create an account. Every user comes with a certain set of factors that help Azure Identity Protection determine the likelihood of a compromised identity. These factors represent the user's baseline behavior. Two of the most commonly used ones are login location and device type.
For example, if an employee usually accesses the company's network or system with their own laptop in the office, then any deviation from this behavior increases their Risk Score.
"What types of risk detection are there in Azure Identity Protection?"
The types of risk detections fall into two categories: risk-type and license-type.
This means that risks are classified based on the type of threat into:
- Sign-in risks, and
- User-linked detections
There are also certain types of risk detection that users only gain access to when they upgrade to Azure AD Premium P2 - these are license-type detections.
To make this easier to understand, here's a quick overview of the various risks Azure Identity Protection covers:
|
Type of detections |
Sign-in risks |
User-linked detections |
|
Premium P2 |
|
|
|
Standard, non-Premium P2 |
|
|
Conclusion
Companies shouldn't spend significant amounts of money on cyber security tools like antivirus software and firewalls if they don't also include identity management in their security scheme.
The reason for that is simple - despite their best efforts, the absence of identity management will leave their systems and their networks vulnerable to attack, and all the other cyber security tools in their tech stack won't protect them from an attack.
A software tool like Azure Identity Protection plays a pivotal role in every organization's security scheme. With it, company stakeholders can rest easy knowing that their employees' identities won't be compromised and attackers won't exploit their authorizations to steal or destroy crucial company data.
So if you'd like to learn how to implement Azure Identity Protection into your organization's security scheme, get in touch with Amaxra or visit our blog to learn more about protecting your business.


Get Started Today
We'll build a secure and complete Microsoft software solution for your business while you concentrate on what's important.
