- Articles
- Easily protect your Microsoft Teams users fro...
Table of Contents
It wasn’t that long ago that Amaxra consultants heard Microsoft SharePoint was a little too secure. To some of our business clients, Slack seemed easier to collaborate with external vendors because it would enable sharing from the corporate network with just a valid email address. SharePoint, on the other hand, was locked down; requiring external viewers to authenticate by submitting two forms of ID and a blood sample. But Microsoft Teams has eliminated all those objections with secure guest accounts—making the sharing of internal corporate resources with external vendors simple.
But what about cybersecurity? There are a few things you need to be aware of when sharing corporate data and resources with guest accounts in Microsoft Teams:
Guest accounts can phish you from a link in Microsoft Teams
Amaxra consultants often act as external vendors for large global enterprises. Some of our clients use Microsoft Teams, enabling Amaxra’s expert consultants to receive secure access to the enterprises’ corporate network. That’s the beauty of Microsoft Teams; enabling secure guest account access to internal data and resources for better collaboration between external vendors.
But taking Amaxra out of the equation for a moment, let’s say you hire an external vendor to build a mobile app for your company. You invite their software developers to collaborate with you in Microsoft Teams but then one of those developer’s Teams accounts either gets compromised by a hacker or the developer just has a falling out with his employer and unscrupulously wants to cause damage as he leaves. The problem is that a compromised external guest account in Microsoft Teams still has access to your company’s internal chat conversations and other sensitive data. A compromised guest account can post hyperlinks to “phishing” websites in the chat of Microsoft Teams. We’ve blogged in the past how hackers use proven psychological techniques to get people to click phishing links, so this is a very real problem.
Guest accounts can trick you with malware in Microsoft Teams
Another potential way a compromised guest account can attack your organization is by uploading malicious files (or “malware”) directly into Microsoft Teams. A shared Word document, Excel spreadsheet, or PowerPoint file from the malicious guest account could contain ransomware, a hacker tool that locks users out of any device that opens the infected file—and the only way to unlock your device is to pay money to the hacker.
The malicious guest account could upload a malware-infected document in Microsoft Teams with instructions for everyone to review. So, everyone in your organization who opens this infected document shared in Teams could find themselves unable to do any work on their laptop or tablet because of ransomware.
Compromised guest accounts are vandals inside your walled garden
Amaxra has blogged in the past about how the cloud, and specifically Office 365, offers “walled garden” cybersecurity protections. The key to successful walled garden cybersecurity is authorization. But as we’ve already established, Microsoft Teams guest accounts are invited then authorized to work inside your secure organization. Because of this, the communication and files shared between external vendors and your internal contributors on Microsoft Teams is considered “safe.” It’s a bit of an oversimplification, but the gist is that the inherent protections Office 365 has against external malware and phishing cybersecurity attacks are lifted because Teams guest accounts are viewed as internal to your organization. If you think of your Microsoft Teams setup as your walled garden, then compromised guest accounts are vandals who are already inside your walls.
How to protect against phishing/malware in Microsoft Teams
One solution Amaxra deploys to our clients to guard against phishing attacks in Microsoft Teams is the Amaxra Office Protect plan. This add-on (delivered for as little as $1 per month/per user) to your Office 365 subscription catches phishing attempts by finding sign-ins from unusual locations, unknown devices, or IP addresses. Office Protect then alerts you of the phishing attempts in a simple, easy to read “single pane of glass” administration console. The inexpensive Amaxra Office Protect plan can be effective against phishing attempts on your corporate network coming from links sent in both Outlook mail and in Microsoft Teams chats.
However, we have found the most successful (and cost-efficient) method to protect Office 365 Business users against both phishing and malware is upgrading them to Microsoft 365 For Business. This upgrade pays for itself quickly because it bundles the Advanced Threat Protection (ATP) cybersecurity normally found in the more expensive Office 365 “E5” enterprise subscription plan along with free upgrades to the latest secure version of Microsoft Windows 10 Professional for your entire organization. Note: there is also a Microsoft 365 for Enterprise but it is a different offering as it includes the Enterprise version of Windows 10.
The ATP solution with Microsoft 365 For Business leverages Microsoft’s investments in cloud-based artificial intelligence to protect your shared files and communications whether initiated in Microsoft Teams, Exchange Online, SharePoint, or OneDrive cloud storage. When your organization enables ATP in Microsoft 365, you’re getting:
- A cloud-based service that helps protect your organization against unknown malware and viruses by providing robust zero-day protection
- Advanced features to safeguard your organization from harmful links in real time
- Detailed reporting and URL trace capabilities for your IT department to track and stop cyberattacks now and in the future
See how Amaxra deploys ATP with Microsoft 365
Amaxra’s clients with Microsoft 365 For Business are set up by default to protect every employee against phishing attacks and malware using ATP policy configurations. For example, we set the ATP Safe Attachments policy to automatically scan every file uploaded into the cloud-based storage used in Microsoft Teams. If you had an external guest account in Microsoft Teams who uploaded a malware-infected file called “Marketing Proposal.pptx” the ATP Safe Attachment policy would warn and block your internal employee from opening the file:
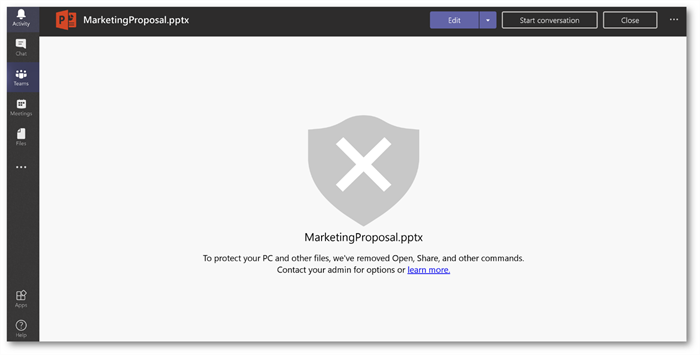
Amaxra also sets up the ATP Safe Links policy to protect against phishing hyperlinks posted in Microsoft Teams. For example, say a malicious external guest account posts a phishing URL in a Microsoft Teams conversation (usually with some “need your approval ASAP” text to try and get the users to hurry up and click):
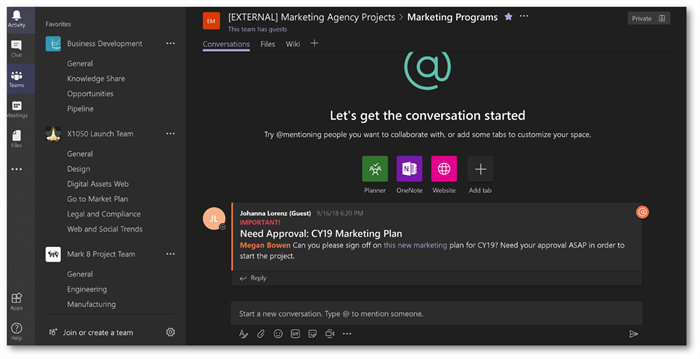
When your internal employee clicks on the link, the ATP Safe Links policy Amaxra configured by default in Microsoft 365 For Business recognizes it as a phishing website and blocks the user from going to the website:
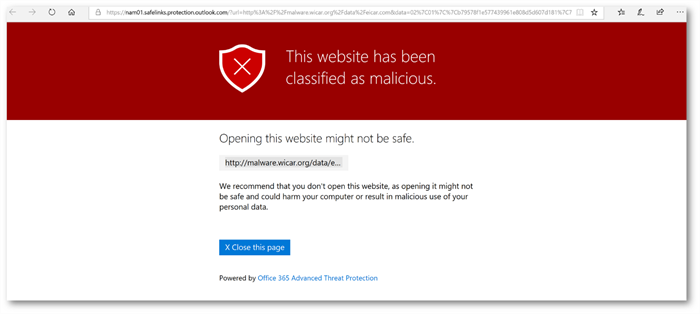
The 2018 Data Breach Investigations Report (DBIR) showed that 39% of malware attacks are ransomware. It only takes a hacker an average of 16 minutes after a successful phishing attempt to gain access to corporate files. Now more than ever it is crucial for all organizations to maximize their limited IT and cybersecurity resources against these threats. Amaxra can help you protect against these threats with a customized deployment of Microsoft 365 For Business with ATP—and show you how it saves you money compared to adding ATP to your existing Office 365 subscription.
