- Articles
- Complete Guide to Azure Virtual Desktop [Serv...
Table of Contents
With more organizations moving to remote-work only or hybrid working environments, the need for robust desktop virtualization software has increased. Recently, solutions such as Windows 365 Cloud PC have emerged, giving users an entire cloud-based PC environment or the ability to access specific applications with no special hardware requirements. However, Azure Virtual Desktop (AVD) is still a more robust solution for larger organizations, such as enterprises, that have variable virtualization needs and want more flexibility and control over the management of the desktop virtualization experience.
For organizations with complex computing needs, Azure Virtual Desktop services provide the customization and computing power transferability that supports effective desktop virtualization for essentially every use case.
This article explores the ins and outs of AVD, including:
- The technology
- Compatibility with different Microsoft operating systems
- Security features
- Requirements to get started with using Azure Virtual Desktop
And much more. Let's get started.
What is Azure Virtual Desktop
Azure Virtual Desktop is a virtual desktop infrastructure (VDI) solution that allows employees to gain secure access to enterprise data and applications remotely. With this remote connection, the exact same experience is provided to the user regardless of the type of device they are using because the host server handles computing.
Introduced in 2019 as a desktop and application virtualization environment, Azure Virtual Desktop used to be known as Windows Virtual Desktop. But after the global health crisis, the solution evolved to run in the cloud and provide more robust security and management simplification. This is why people sometimes call the solution “Azure Windows Virtual Desktop.” The evolution of AVD created a more effective remote working solution that makes the deployment and management of desktops easier for organizations.
Full Device Support
Running in the Azure cloud environment, AVD works seamlessly with all of your organization's existing applications and devices with native client support. So, if one employee prefers using a Mac over a PC, it doesn't affect the AVD experience. Mobile support for Android and iOS is available as well. HTML 5 is also supported to enable access to remote desktop environments and applications from any modern web browser. What's more, regardless of the device someone uses, the experience will be the same. When using a virtual desktop, apps can be pinned to the taskbar or accessed from the Start menu, and the apps look and feel like local apps.
Eliminates the Complexity of Setting up a Virtual Desktop Environment
Setting up a virtual desktop environment has traditionally been expensive, time-consuming (often taking weeks or months to deploy), and complex. Azure Virtual Desktop services provide the backend remote desktop infrastructure to allow roles such as your Azure Virtual Desktop gateway broker, load balancing, and diagnostics to be delivered as a fully-managed service. In addition, any size VM can be configured in Azure Virtual Desktop and control the density of users based on workload requirements. In other words, you can gain efficiency by having multiple users on one VM.
FSLogix Technology Integration Makes Working with Stateful Apps Painless
FSLogix is a Microsoft technology built to store roaming user profiles in the cloud. Because each user's profile data is containerized in a separate virtual disk, users have a much better experience using stateful applications. These virtual disks attach in real-time to a session, providing user data immediately. Here are two examples:
- Inbox data in Outlook updates in real-time, meaning that when the user opens the application, they don't have to wait for updates to load; they will immediately see their inbox.
- Another example is regarding OneDrive and File Explorer. Stored files can also be accessed on-demand with FSLogix, ensuring that a user's files are always available on the virtual desktop environment. In short, FSLogix makes local files persistent and feels like they are running off the local C: drive.
Ability to Achieve Low Latency with Proximity Placement Groups
While placing virtual machines (VMs) in a single location reduces the physical distance between instances, it's not a sustainable solution for distributed organizations. When VMs span multiple data centers, it impacts your virtualization environment in terms of network latency. Latency is the time (usually measured in milliseconds) it takes for a client device to send data to the origin server and receive a response. So, if your client device is a laptop in Seattle, then it's preferred that your VM is hosted on a server located on the west coast rather than in Miami or Boston to reduce latency. To ensure that applications and desktops run as smoothly as possible with little interruption, it's important that organizations consider latency, as high latency can significantly impact user experience, even making applications unusable in certain circumstances.
Proximity placement groups are the solution. To get VMs as close as possible and achieve the lowest latency, VMs can be placed in a proximity placement group, which is a logical grouping that ensures that compute resources are physically located close to each other.
Azure Virtual Desktop services provide proximity placement groups as a resource within the software. The following can be achieved with a proximity placement group:
- Low latency between stand-alone VMs.
- Low latency between stand-alone VMs in a single availability set (for SQL servers) or a virtual machine scale set (for managing a group of load-balanced VMs). Multiple compute resources in a single placement group can support a multi-tiered application.
- Low latency between multiple application tiers using different types of hardware.
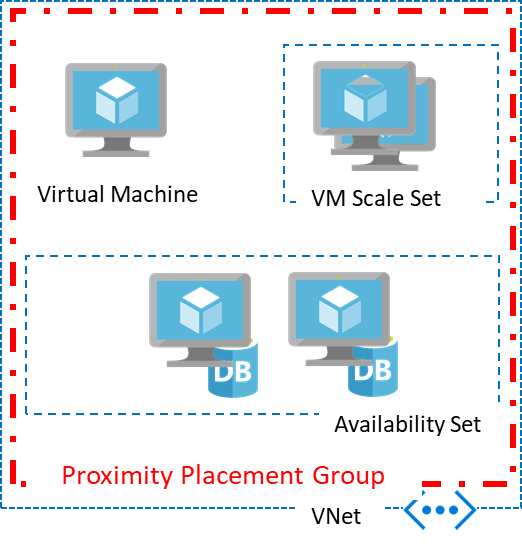
Essentially, different types of systems, or availability sets, scale sets, etc., can be put in a group together to get them as close as possible, reducing latency as much as possible.
While this is an effective solution, there are potential limitations. For instance, availability zones. Let's say that within an Azure environment, there are regions with hundreds of miles between them. Inside those regions are data centers, and depending on how many data centers there are and where exactly those data centers are located, there are availability zones. Because we're dealing with physical hardware in these data centers, it's not effective to have multiple proximity placement groups in different availability zones since it won't help latency due to the proximity of the equipment.
Azure Virtual Desktop Operating Systems
There are different Microsoft-supported operating systems available as session hosts for Azure Virtual Desktops and applications with AVD. Different operating systems can also provide different host pools if flexibility is needed. The following 64-bit versions of Windows operating systems are supported (table provided by Microsoft):
|
Azure Virtual Desktop operating systems |
User access rights |
|
License entitlement:
External users can choose per-user access pricing instead of license entitlement. |
|
License entitlement:
Per-user access pricing is not available for Windows Server operating systems. |
Some important notes to keep in mind:
- Virtual desktop in Azure doesn't support 32-bit operating systems or software not listed in the above table
- Support for Windows 7 ended on January 10, 2023
- Ephemeral OS disks for Azure VMS are not supported
Ensuring that your organization has the right mix of licenses needed to facilitate work while still being cost-effective is paramount. But on the other hand, Microsoft licensing is difficult to navigate. There are always changes being made to licensing, and auditing your licenses regularly is time-consuming for IT teams. Amaxra can be your Microsoft licensing partner, ensuring that you're only paying for the licensing you need, saving your organization time and money.


Need Help with Microsoft Licensing?
Leave your Microsoft licensing, security, and software solutions to us so you can concentrate on moving your business forward.Drop Us a Line
Azure Virtual Desktop Security

Desktop virtualization provides an effective way to manage users' desktops centrally, without IT having to connect individually to each desktop to perform updates, security fixes, and more. Further, because desktop virtualization separates operating systems, data, and applications from local hardware and runs them on a virtual server instead, effectively separating the computing environment from user devices, it's much easier for IT teams to manage security at scale.
However, while a virtual desktop in Azure has many advanced security features, it's important to understand which security features Microsoft manages and which security features the customer is expected to manage.
The following table (provided by Microsoft) quickly outlines responsibilities:
|
Security need |
Is this the customer's responsibility or Microsoft's? |
|
Identity |
Customer |
|
User devices (mobile and PC) |
Customer |
|
App security |
Customer |
|
Session host operating system (OS) |
Customer |
|
Deployment configuration |
Customer |
|
Network controls |
Customer |
|
Visualization control plane |
Microsoft |
|
Physical hosts |
Microsoft |
|
Physical network |
Microsoft |
|
Physical datacenter |
Microsoft |
Of course, AVD runs in an organization's Azure environment. This means that the security of the Azure environment directly affects AVD, so it's important to ensure that IT teams are considering this and implementing best practices for securing the Azure environment as a whole and then looking granularly at AVD itself. Azure advanced threat detection provides a suite of tools that protect sensitive data by detecting, preventing, and responding to threats.
Azure Virtual Desktop Security Best Practices
There are a number of Azure Virtual Desktop security best practices that organizations should follow, which are listed below and described in more detail:
Use Multi-Factor Authentication and Conditional Access
To ensure that the right users are signing into your organization's virtual desktop environment, it's recommended that Azure Active Directory (AD) Multi-Factor Authentication (MFA) is used. This prompts the user who wants to sign in to provide another form of authentication besides their username and password. The Microsoft Authenticator app, for instance, will either provide verification through a passcode or PIN that the user needs to enter or use the device itself (where the user needs to enter their device's PIN, use the fingerprint, face unlock, or whatever security feature they have enabled for device access) to verify their identity. Encouraging users to use a password manager such as LastPass is also a good idea to ensure that strong passwords are always used on every device.
MFA on AVD can be enforced using Conditional Access to control when and how access is granted to different areas, like if the AVD web client is used when mobile applications are accessed when a desktop client is accessed, and more.
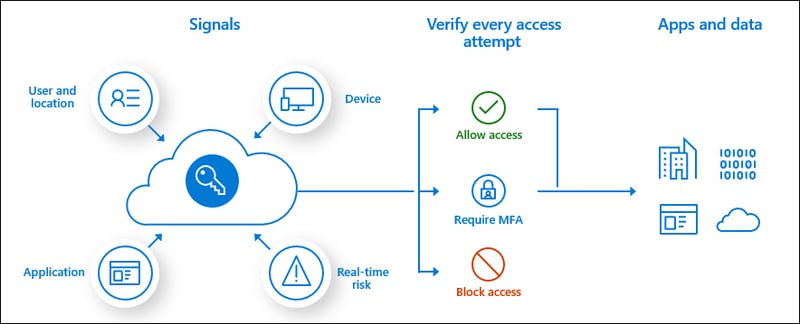
Azure AD Identity Protection is another essential security tool that detects identity-based risks, such as compromised identities and security credentials, so security teams can investigate and take appropriate action.
Collect Audit Logs
Collecting audit logs gives administrators a bird's eye view of the user and admin activity on a virtual desktop in Azure. Examples of different key audit logs include:
|
Audit log name |
Description |
|
|
|
|
|
|
|
|
|
Monitor Usage with Azure Monitor
Virtual desktop and remote app usage can be monitored with Azure Monitor. Health alerts can be created so IT administrators and other stakeholders receive notifications when necessary.
Encrypt your VM
Fully utilizing encryption for your virtual machines is essential for a secure workspace. Different types of encryption available include Azure Disk Encryption (ADE), Server-SIde Encryption (SSE), and encryption at host.
Azure Virtual Desktop Requirements

Aside from having one of the compatible operating systems listed previously in this article, several other requirements are needed before your organization can start using Azure Virtual Desktop. These requirements include:
An Active Azure Account
You'll need to sign up for an Azure account to access various Azure services, including Azure Virtual Desktop. If you think of Azure like an umbrella, your main account allows you to customize everything underneath it-meaning you can create multiple other granular subscriptions, manage accessible resources under those subscriptions, associate an Azure subscription with an Azure Active Directory tenant, and more.
An Identity Provider
This is where Azure Active Directory comes in. Azure Virtual Desktop requires users to connect to a session host, which is enabled through Azure Active Directory. Users can connect to a session host via an Azure AD tenant or an Active Directory domain (which can be enabled using Active Directory Domain Services as an additional option).
A Supported Operating System and Licenses
A list of compatible operating systems is listed earlier in this article, generally consisting of Windows 10 or 11 Enterprise or Windows Server. In addition to having a supported operating system, the right licenses are also required. The supported licenses are listed earlier in this article as well.
Network connection. The following network requirements are needed for users to connect to Azure Virtual Desktop successfully:
- A virtual network that's in the same Azure region as the session host.
- The virtual network that you're using must also be able to connect to your domain controllers and relevant DNS servers if you're using AD DS or Azure AD DS.
- Session hosts and users must be able to connect to the Azure Virtual Desktop service, which uses the TCP on port 443 to a specific list of URLs, which can be found in the required URL list.
A remote desktop client. Once everything else is set up, users will need some sort of software to be able to access Azure Virtual Desktop. Remote desktop clients are available for various operating systems and devices, including Windows, web browsers, macOS, iOS and iPad, and more.
Conclusion
These days, remote working is the new regular working environment for many organizations, including large enterprise businesses. As a result, it's not uncommon for businesses to have highly distributed teams with employees worldwide. The challenge, then, is facilitating a digital work environment that embraces remote work but also maintains the security and accessibility that businesses need to keep sensitive information safe while still ensuring that their employees can be productive.
That's where solutions like Azure Virtual Desktop come in. As a flexible, holistic solution for remote work enablement, AVD has the customization capabilities needed to make the solution work for any organization.
If your organization is ready to build your cloud-based, remote work solution with Microsoft Azure, Amaxra can help.
Contact Amaxra today for a consultation.


Get Started Today
We'll build a secure and complete Microsoft software solution for your business while you concentrate on what's important.
