- Articles
- Prevent Windows Defender Advanced Threat Prot...
Table of Contents
Emails remain a primary mode of communication for all organizations.
From onboarding details for new hires to scheduling team meetings with personal login information, emails serve as the de-facto medium for sending sensitive workplace data.
Cybercriminals know this, too.
With the possibility of your company's image being tarnished from one data breach and 96% of phishing attacks arriving via email, the importance of good email security couldn't be more glaring.
This article will guide you through:
- The definition of email phishing
- When and why it occurs
- How to use Windows Defender to prevent email phishing
What Is Email Phishing?

Email phishing is when cyber criminals send malicious emails to trick people into scams. These emails are designed to persuade users to reveal financial information, system credentials, or other sensitive data. From asking for your personal information to attaching viral-infected files, attackers impersonate legitimate organizations and primarily aim to steal account credentials and corporate trade secrets.
Spear phishing emails are often sent to specific people within an organization.
Usually, high-privilege account holders are the prime targets of spear phishing emails that trick them into providing sensitive information, sending money, or downloading malware.
When attackers use spear phishing tactics to go after a large, high-profile target, such as the C-suite, it becomes whaling - the analogy makes sense when you think about it.
Cybercriminals use email primarily because it's an easy entry point to other accounts and devices, and it's largely prone to human error. All it takes is one misguided click to cause a security crisis for an entire organization.
Most phishing attacks include:
- Malicious web links: these take users to impostor websites or sites infected with malware. They're usually disguised as trusted links and embedded in an email's logos and images. For example, emails with a link to "validate your credentials" are sent from an unrecognizable domain that takes you to a page to input your details.
- Virus-infected attachments: these seem like valid attachments, but instead, they release malware into your system files once you download or open them. The infection can lock the files in your PC and make them inaccessible or monitor your keystrokes. It can also extend to other PCs on the company network.
- False data entry forms: request for you to fill in sensitive data such as IDs, passwords, credit card information, and address which cybercriminals can use for harmful purposes after you submit the details. For example, attackers can use a fake checkout page asking for your card payment information for identity theft.
Phishing trends and techniques
From fake invoices to compromised business emails, malicious attackers use several phishing techniques to get into your infrastructure.
Hiring a cyber security consultant while using Windows Defender is an extra layer of security, especially when assessing your network's cyber security risk.
With a good grasp of what malicious attacks look like, employees could stop a phishing attack in 19 minutes.
Phishing trends and techniques include:
Business email compromise
This scam usually targets businesses that often work with foreign distributors or frequently perform money wire transfers. Cyber attackers try to access a company's internal network via spear phishing by using a domain similar to the targeted company's and spoofing their email to persuade users to reveal personal account information for money transfers.
Downloads
These are similar to virus-infected attachments, but rather than introduce malware into your systems. These attachments contain a prompt. The message requests that you sign into a site such as a file-sharing website to access the document. When you use your sign-in credentials on such sites, attackers save your information.
Invoice phishing
For this scam, the email states that you have an outstanding invoice that you need to settle. The invoice usually looks like it's from a known and trusted vendor company. With terms aimed at increasing your sense of urgency, they provide a link for you to access and pay your invoice. Here, attackers can steal your personal information and funds.
Payment/delivery scam

Here, attackers request your credit card details or other personal payment information under the disguise of a familiar vendor or supplier. The cybercriminals say you should provide such information to take the delivery of your ordered goods but don't provide any information on the items you purchased from them.
Tax-themed phishing scams
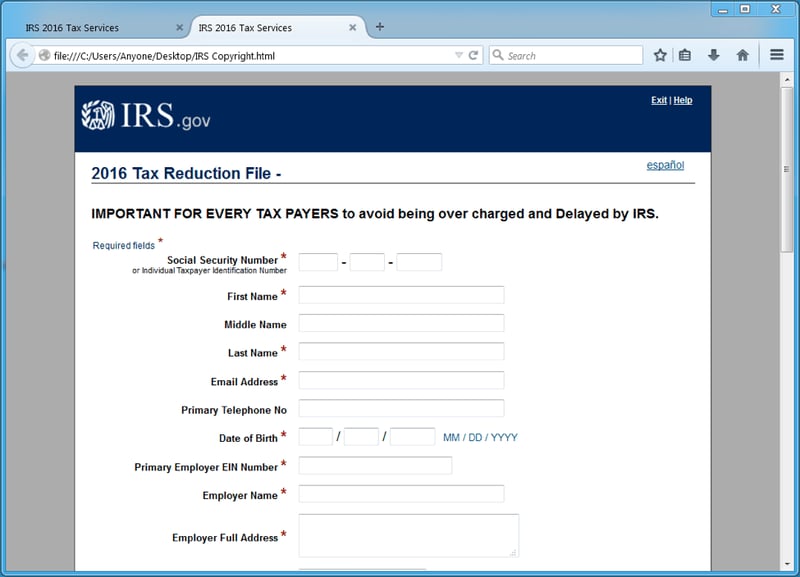
The most common type of this technique is the IRS phishing scam. In this case, you receive an urgent email indicating that you owe money to the IRS. The email usually threatens legal action if you don't access a site within a short timeframe. When you input your payment details on the site, attackers can use your personal information to empty your account.
Windows Defender helps you detect phishing emails with its machine learning feature, which lists the contacts you frequently communicate with and differentiates suspicious from typical behavior.
How to spot phishing emails
Most phishing scams have several common features or indicators that help you spot them.
Phishing emails usually:
Request your sensitive information via email
Once you get an email that links or asks for passwords, credit card information, credit scores, or tax numbers, treat it with caution and report it because it's a scam. Legitimate companies would not request your login details via email.
Use generic greetings such as "Dear account holder" or "Dear Sir/Madam."
Phishing emails are as generic as possible with little to no personalization. Companies with your information would personalize the email with your account name. They'd most likely call you if the issue were that urgent.
Do not use a domain email address
Legitimate companies use email domains that are the replica of their company name. Domains prove their authenticity, so one of the best ways to spot a phishing email is by first looking at its domain address. Most phishing email domains add numbers after the company name or use an entirely different one.
Here are some of the top email phishing subject lines that people click on globally:
- Authorize Pending Transaction on your Wallet
- HR: Registration for COVID-19 Study
- IT: End of Year Password Policy
- HR: Code of Conduct
- Your Benefit Account Has Been Updated
When and Why Does Email Phishing Occur?

Keeping your employees safe while working from home can be challenging because there is a higher risk of impersonation.
A phishing campaign usually starts with a malicious email message. This attack is disguised as a message from a legitimate company.
Cybercriminals try to mimic as many aspects of the actual company as possible. The higher the similarity with the real deal, the higher the chances that the targeted employee will fall for the scam.
An attacker's goals can vary from stealing personal or sensitive company information to freezing critical assets and demanding a ransom.
Most phishing scams feature a sense of urgency in the message, which could threaten the user with:
- Account suspension
- Money loss
- Job position loss
Employees that fall for scams are usually affected by the sense of urgency and avoid taking time to assess the email. Organizations must often train staff to identify the latest phishing strategies and keep up with how phishing evolves.
Check out this analysis of links in phishing-like emails to better understand how fake emails appear.
Windows Defender Advanced Threat Protection Email Phishing Prevention Tips

Windows Defender Advanced Threat Protection is a Microsoft post-breach solution that continuously monitors your network to alert you when a breach occurs. From guiding you through the steps to secure the breach to detecting, investigating, and responding to security threats on your network, Windows Defender Advanced Threat Protection helps you evaluate and spot existing weaknesses in your system.
It's crucial to note that Windows Defender Advanced Threat Protection is not an anti-virus product; it's a post-breach solution.
For Windows Defender Advanced Threat Protection email phishing, securing your network involves:
- Alerting you once the threat through the phishing email is identified and tracking how it entered your network
- Stopping the threat from spreading to the rest of your network by isolating it
- Updating your Microsoft anti-virus to record, learn and be in a better position to tackle the malware or mode of attack.
When Windows Defender is not resolving breaches, it inspects your infrastructure round the clock to detect any vulnerabilities and alert you. It also recommends remedial measures for your system.
From guarding your system against unsafe attachments to expanding protection against malicious links, Windows Defender complements the security features of Exchange Online Protection to provide better zero-day protection.
Windows Defender Advanced Threat Protection covers other Microsoft products, including:
- Teams
- SharePoint Online
- OneDrive for Business
To protect your network holistically, read our comprehensive Windows Defender Advanced Threat Protection guide to learn more about its features, pricing, and license requirements.
Configure anti-phishing policies
These policies enable you to configure anti-phishing protection settings for your Microsoft environment to strengthen your cyber security.
This table shows the anti-phishing policy features available in Exchange Online Protection and Windows Defender.
|
Anti-phishing policy feature |
Availability in Exchange Online Protection |
Availability in Windows Defender |
|
Automatically created default policy |
✔ |
✔ |
|
Create custom policies |
✔ |
✔ |
|
Default policy settings |
✔ |
✔ |
|
Spoof settings |
✔ |
✔ |
|
First contact safety tip |
✔ |
✔ |
|
Impersonation settings |
- |
✔ |
|
Advanced phishing thresholds |
- |
✔ |
Impersonation settings
These settings help protect your network from emails with domains similar to your company's and have a high likelihood of impersonating a department or team member.
You can select the users and domains to protect from impersonation and preset actions that are flagged as impersonation attempts, such as:
- Redirecting the message to other email addresses
- Moving it to the recipient's Junk Email folders
- Quarantining the message
- Delivering the message and adding different addresses to the Bcc line
- Deleting the message before it's delivered
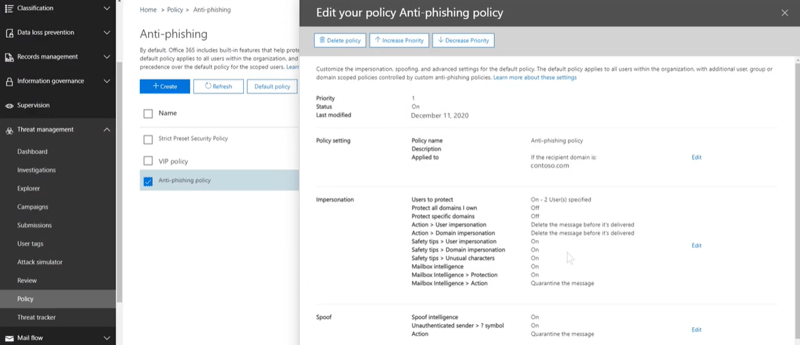
In each anti-phishing policy, you can have a maximum of 50 custom domains and 350 protected users. Windows Defender blocks any emails that impersonate the ones you have specified in your policy.
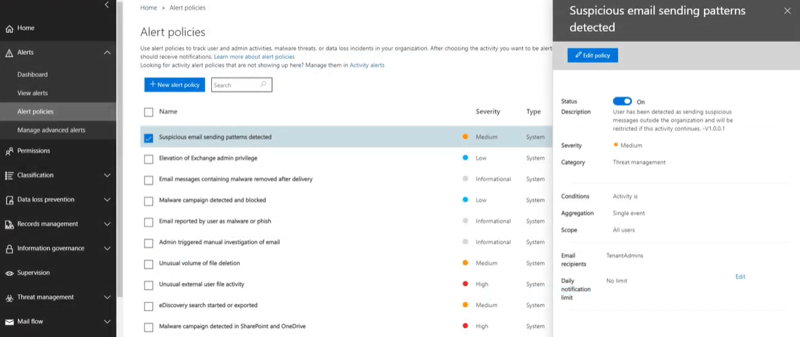
You can also configure alert policies to notify your security team when suspicious email forwarding activity is detected.
Turn on Safe Attachments
With Windows Defender, you can enable Safe Attachments, which provides an extra layer of security for your email attachments after the anti-malware protection has scanned them in Exchange Online Protection.
Safe Attachments opens the files in a virtual environment before they are delivered to the recipients.
Note: You can also enable Safe Attachments in SharePoint, OneDrive, and Microsoft Teams to detect and block existing files that have been identified as malicious in team sites and document libraries.
To turn on Safe Attachments for SharePoint, OneDrive, and Microsoft Teams using Windows Defender, use the following steps:
- From the Windows Defender portal, go to Policies & rules > Threat policies > Safe Attachments in the Policies section
- On the Safe Attachments page, click Global settings and go to the Protect files in SharePoint, OneDrive, and Microsoft Teams section
- Click on the "Turn On" toggle to move it to the right and save your settings once you finish
Simulate attacks to your network
Simulated attacks help you run realistic scenarios in your organization. You can use them to pinpoint vulnerable users in your network and address leaks accordingly to prepare yourself better for an actual attack.
With Windows Defender's Attack simulation feature, you can empower your employees to be more secure against phishing attacks by:
- Measuring users' awareness of phishing risks
- Providing insights and actionable recommendations to use hyper-targeted training to improve user behavior
- Track behavioral change through repeated simulations
Read this guide to learn more about how you can simulate a phishing attack with Attack simulation training in Windows Defender.


Need Help with Microsoft Licensing?
Leave your Microsoft licensing, security, and software solutions to us so you can concentrate on moving your business forward.Drop Us a Line
How to Report Windows Defender Phishing Emails

If you notice a suspicious email or file, you should immediately report and investigate it - by being proactive, you can catch malicious attacks early and improve your company's security.
There are several methods of reporting suspicious emails to Microsoft. Here's an overview:
|
Method |
Submission Type (Authorization) |
Description |
|
Use the Submissions portal to submit the suspected spam, phish, URLs, or email attachments to Microsoft |
Admin |
The recommended reporting method for admins in organizations with Exchange Online mailboxes. |
|
Enable the Report Message or the Report Phishing add-ins |
User |
Works with Outlook and Outlook on the web. You can configure reported messages to be copied or redirected to a specific mailbox. |
|
Report false positives and false negatives in Outlook |
User |
Send the safe emails that have been wrongly blocked or sent to junk, and any unwanted email or phish that was let through to Exchange Online Protection using the Report Message feature. |
|
Use mail flow rules to see what users are reporting to Microsoft |
Admin |
Create a mail flow rule (also known as a transport rule) that notifies you when users report messages to Microsoft for analysis. |
|
Submit files for analysis |
Admin |
Submit email attachments and other suspected files to Microsoft for analysis. |
While you can use the Submissions portal to report:
- Suspected spam, phishing emails, and URLs
- Legitimate emails getting blocked
- Email attachments
You need admin access under the Security Administrator or Security Reader role in Windows Defender.
Once you have admin access, you can report phishing emails by following these steps:
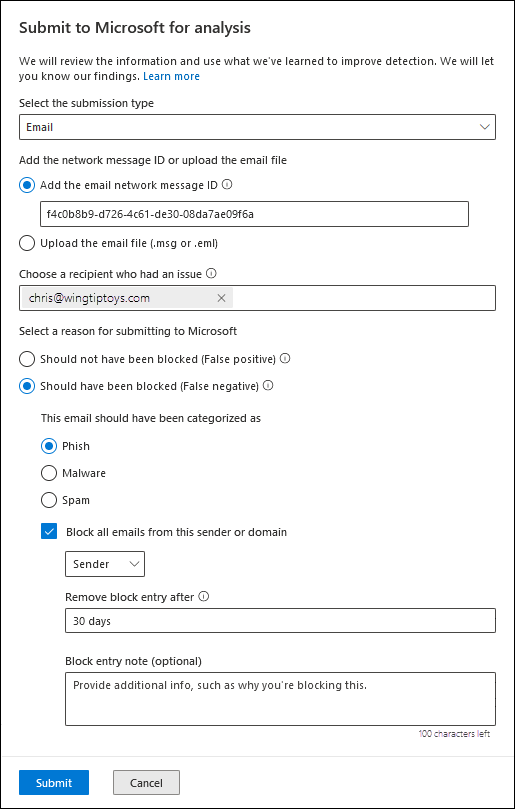
- On the Submissions portal, select the Emails tab.
- Then, click Submit to Microsoft for analysis.
- From the flyout that appears, select the following information:
- Select the submission type: Verify that Email is selected.
- Add the network message ID or upload the email file: Select one of the following options:
-
- Add the email network message ID: This is a GUID value in the X-MS-Exchange-Organization-Network-Message-Id header in the message or the X-MS-Office365-Filtering-Correlation-Id header in quarantined messages.
- Upload the email file (.msg or .eml): Click Browse files. Find and select the .eml or .msg file in the open dialog, then click Open.
- Choose a recipient who had an issue: Specify the recipient you would like to run a policy check against.
- Select a reason for submitting to Microsoft: Verify Should not have been blocked (False positive).
-
- The email should have been categorized as: Select Phish since you are reporting a phishing email. You can also choose other options like Malware or Spam.
- Block all emails from this sender or domain: Select this option to create a block entry for the sender in the Tenant Allow/Block List. If you select this option, you can:
- You can select a Domain instead of the default Sender.
- Remove block entry after Select from 1 day to Never expire. You can also set a specific date
- After verifying that everything looks good, click Submit, and then click Done.
After your settings, you should have something that looks like this:
Besides reporting emails, attachments, and URLs, you can use the Submissions portal to:
- View admin and user submissions to Microsoft
- Undo user submissions
- Convert user-reported messages from the custom mailbox into an admin submission
- View associated alert for user and admin email submissions
Visit Microsoft's learning page to learn more about the steps involved in each process or consider hiring a Microsoft Gold Partner (a company that has earned the highest level of company customer care and collaborative relationship with Microsoft) to help you optimize the process of reporting phishing emails while you focus on your core business.
Windows Defender Advanced Threat Protection Email Phishing FAQs
"Does Windows Defender protect against phishing?"
Yes, Windows Defender protects your network against phishing.
It monitors your mail system in real time and provides remedial measures to resolve breaches with minimal downtime. Key features include:
- Anti-phishing policies that help you protect specific users and domains
- Safe attachments to tackle malicious files
- Simulated attacks to evaluate and increase your organization's cyber security.
"How do I know if a Microsoft security alert is real?"
If you receive a security alert from Microsoft, you can rest assured it's legitimate if the email:
- Comes from the address "account-security-noreply@accountprotection.microsoft.com"
- Clearly indicates that it's from the Microsoft account team
- Requests that you verify your identity with a security challenge using an OTP or Authenticator app
"What is an incident in Microsoft Defender?"
An incident in Microsoft 365 Defender is a collection of correlated alerts and associated data that make up the story of an attack. Microsoft 365 Defender automatically normalizes and analyses signals and related events across multiple domains and fuses them into incidents that provide a complete view and context of an attack in a single dashboard.
Enhance Your Email Security by Collaborating With a Microsoft Gold Partner
Securing your infrastructure from email phishing helps you to:
- Protect your organization's image and credibility
- Maintain operational efficiency as you avoid downtime from cyberattacks
- Avert expenses of trying to settle successful attacks
You can make the best use of Windows Defender Advanced Threat Protection by partnering with Amaxra.
We are a Microsoft Gold Partner with proven expertise, and we have years of experience supporting clients with Microsoft implementations, particularly those aimed at securing their Windows environments.
Contact us to learn more about how to use Windows Defender Advanced Threat Protection's features and pick the right plan to maintain optimum email security in your company.


Get Started Today
We'll build a secure and complete Microsoft software solution for your business while you concentrate on what's important.
Contact Us

A Comprehensive Beginner's Guide to Cyber Security
Discover the latest cyber security threats and proactive measures for protection.
Empower your organization with knowledge and secure your digital assets effectively.
